Guide
7 Most Powerful CyberSecurity Software Tools

The following is a list and comparison of the top five cybersecurity software programmes available to protect your company from online threats:
For the sake of both a company’s and an individual’s cyber safety and privacy, investing in cybersecurity software is essential. Cybersecurity refers to the approach that is used to defend a network, system, or applications from being attacked by hackers using the internet. It is used in order to prevent unwanted access to data, cyberattacks, and identity theft.
The term “cybersecurity” encompasses a wide range of subfields, including application security, information security, network security, disaster recovery, and operational security, among others. It is necessary to keep it updated for the many different kinds of cyber threats, such as ransomware, malware, social engineering, and phishing.
Types Of CyberSecurity Tools
CyberSecurity Software can be categorized into different types as mentioned below:
- Network Security Monitoring tools
- Encryption Tools
- Web Vulnerability Scanning tools
- Network Defence Wireless Tools
- Packet Sniffers
- Antivirus Software
- Firewall
- PKI Services
- Managed Detection Services
- Penetration Testing
How Important Is Cybersecurity?
The findings of the study carried out by Mimecast might help shed light on the significance of ensuring network security. It is said that there has been a spike of 26 percent in ransomware, that 88 percent of businesses have seen email-based spoofing, and that 67 percent of enterprises have claimed that there has been a rise in impersonation fraud.
Using a public Wi-Fi network makes the device you’re using or the data it stores more susceptible to assaults. According to study carried out by Norton, 54% of individuals who use the internet do so while connected to a public Wi-Fi network, despite 73% of respondents being aware that connecting to a public Wi-Fi network, even if it is password secured, is risky business. All of these numbers demonstrate that there is an urgent need for improved cybersecurity.

When choosing a Cybersecurity tool, it is important to take Cyber Resilience into consideration. Cyber resilience entails making every attempt to thwart the danger while simultaneously striving to minimise the damage that would be caused by an attack if it were to be successful. Because of this functionality, both business and email communication may be maintained without any interruptions.
List Of Best CyberSecurity Tools
The most widely used tools for cyber security are given below. These tools are utilised all around the globe.
#1) SolarWinds Security Event Manager
Excellent for both small and big companies.
SolarWinds Security Event Manager offers a fully functioning trial version for a period of 14 days at no additional cost. The device may be purchased for a starting price of $4500.
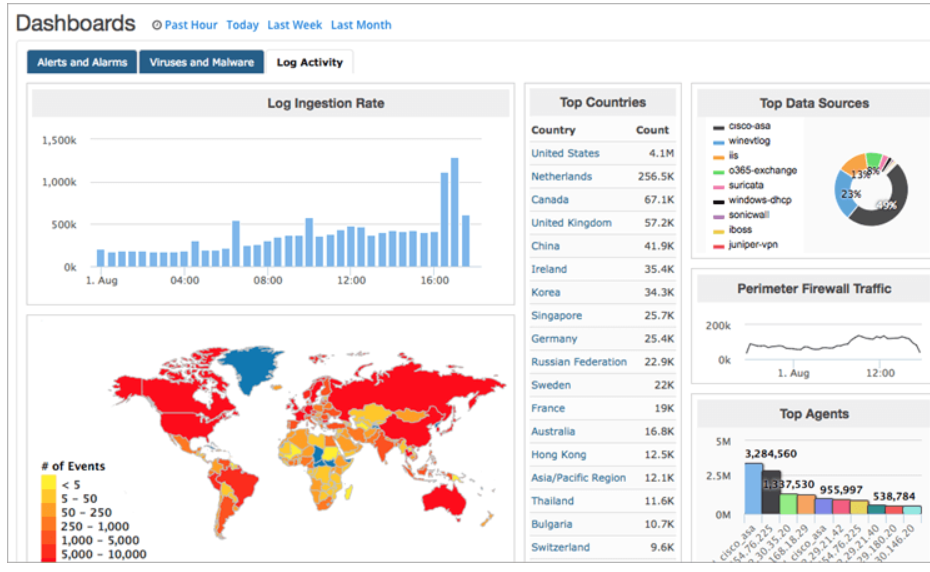
SolarWinds Security Event Manager is an intrusion detection solution that can monitor both networks and hosts. It is capable of doing real-time monitoring, reacting to security risks, and reporting on such threats. It has log search features that are well indexed. It is a scalable system that runs on the cloud.
Features
- There will be consistent revisions made to the threat intelligence.
- It includes functionality for the Security Information and Event Manager.
- It supports Log correlation and Log event archiving, among other useful functions.
- It gives users access to an extensive collection of tools for integrated reporting.
The Solarwinds Security Event Manager is a cloud-based solution that was built for Managed Service Providers as an all-in-one solution of the SIEM tool. The solution was given the verdict that it is an effective SIEM tool.
#2) Intruder
Excellent for both small and big companies.
Intruder Pricing: A 30-day Free trial is offered. There are three different price tiers available, including Essential, Pro, and Verified. Get in touch with them if you want more information about their price options.
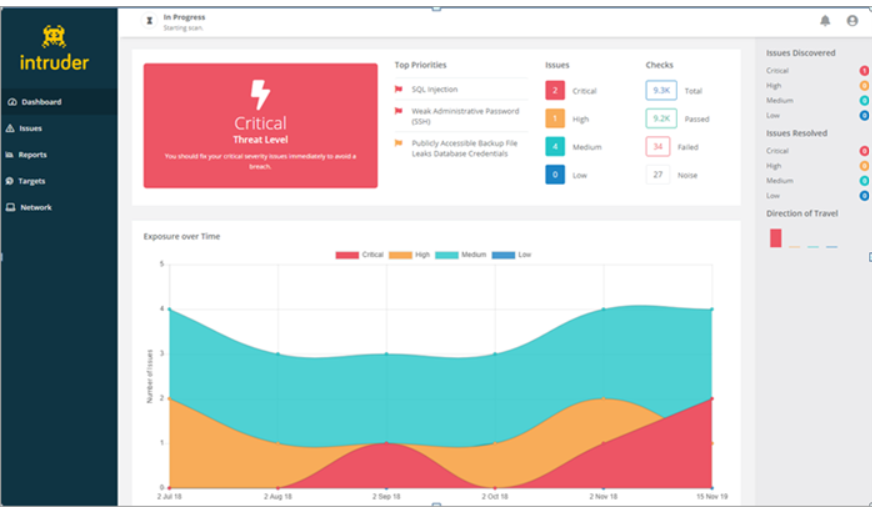
Intruder is the most popular cloud-based network vulnerability scanner, and it may assist you in locating the gaps in cybersecurity protection that exist inside your most vulnerable systems. This can help you prevent expensive data breaches. It is the best answer for the problems you are having with cybersecurity. It will help you save a significant amount of time in the long run.
Features
- Over 9,000 security vulnerabilities.
- Unlimited scans on demand.
- Unlimited user accounts.
- Checks for web application flaws such as SQL injection and Cross-site scripting.
- Emerging threat notifications.
- Smart Recon
- Network view
- PCI ASV scans available.
Conclusion: Intruder is a comprehensive answer to all of your concerns about online safety.
#3) Syxsense
This solution is ideal for businesses of all sizes.
The pricing for Syxsense Secure begins at $960 per year for ten different devices.
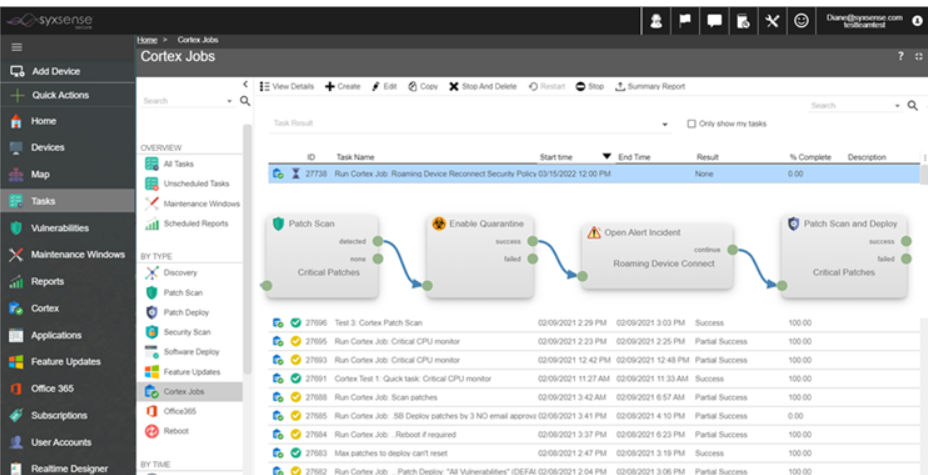
Syxsense Secure is an endpoint security system that combines security scanning, patch management, and remediation into a single interface that is hosted in the cloud. This makes it possible for IT and security teams to prevent breaches with only one security solution.
Features
- Scan for Vulnerabilities: Our vulnerability scanner may help you prevent cyberattacks by analysing authorization problems, security implementation, and antivirus software.
- Repair and replace everything: With support for all of the main operating systems, you can automatically deploy OS fixes and patches from third parties, in addition to Windows 10 feature updates.
- Quarantine Devices: Isolate the endpoint, disable any malicious processes running on it, and prevent the infection from spreading by blocking connectivity between an infected device and the internet.
The verdict is that IT and security teams are now able to automatically communicate in a single interface to identify and shut down threat paths. This is a world first.
#4) Perimeter 81
This solution is ideal for businesses of all sizes.
Pricing for Perimeter 81 The most reasonably priced plan offered by Perimeter 81 begins at $8 per user per month. Additionally, there is a premium plan that costs $12 per user per month, and a premium plus plan that costs $16 per user per month. You also have the choice to proceed with the customised business plan for your company.
The moment we had a cursory look at all of Perimeter 81’s cutting-edge network security capabilities, we were certain that this was the software that we needed to have. Your company will be better able to defend itself against a far wider variety of potential dangers if you use this programme since it provides its users with a vast array of cybersecurity capabilities.
The programme streamlines the process of controlling and safeguarding the integrity of your network by providing remarkable features such as device posture check, web blocking, access to Zero Trust Network, and multi-factor authentication.
Features
- Using the firewall as a service may help ensure the safety of network traffic in all contexts.
- Encryption, two-factor authentication, and single sign-on may help you achieve multi-layered security.
- A unified management and monitoring strategy implemented by a single management plan.
- Using Automatic Wi-Fi Protection, you may prevent connections from being made to unauthorised wireless networks.
Verdict: When you purchase Perimeter 81, you have access to a cloud-based cybersecurity application that offers a multitude of security capabilities that significantly ease the process of safeguarding and maintaining the network. The programme is not only very easy to install and use, which is exactly why we have it listed so high on our list, but it is also quite simple to deploy.
#5) Acunetix
Acunetix is ideal for use by pentesters, online experts, commercial clients, and small enterprises.
Pricing for Acunetix: Acunetix provides the solution with three different pricing plans, which are referred to as Standard, Premium, and Acunetix 360 respectively. You may receive a quotation for price specifics. A demo is also available on request.
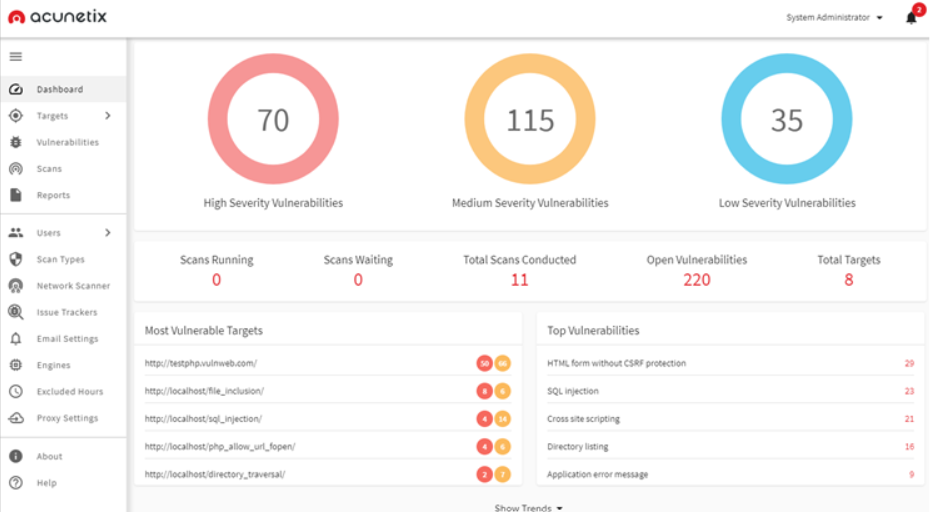
Acunetix is the answer to securing your websites, online apps, and application programming interfaces (APIs). This application security testing tool is able to scan all sites, web apps, and complicated web applications, as well as uncover over 7K vulnerabilities.
It has features for managing vulnerabilities right out of the box. Acunetix gives users the choice to install their software either on their own servers or over the cloud.
Features
- Acunetix makes use of cutting-edge technology for macro recording, which will be of assistance in scanning complicated multi-level forms and password-protected sections of the website.
- It does an analysis to determine how serious the problem is and quickly delivers ideas that may be put into practise.
- It offers the capabilities of scheduling and prioritising the full scans and incremental scans.
The verdict is that Acunetix is a user-friendly and straightforward solution. It is able to execute scanning at a breakneck speed. Acunetix may be incorporated into your existing infrastructure in an effortless manner.
#6) Netsparker
The ideal customers for Netsparker are mid-sized to enterprise-level companies.
Pricing for Netsparker is available, and a quotation may be obtained for further information. Standard, Team, and Enterprise are the three different price tiers that are available for this product.
Enterprises may benefit from using Netsparker since it provides a method for evaluating application security. It provides the capabilities and features necessary for automated security testing at every stage of the software development life cycle (SDLC). Automation, visibility, accuracy, scalability, and security are just few of the characteristics that Netsparker has.
Features
- Developers may get assistance from Netsparker in developing code that is more secure for the environment it is being used in.
- It conducts thorough scans and has the ability to find vulnerabilities in a short amount of time.
- It combines elements of signature and behavior-based testing into a single process.
- It employs a one-of-a-kind scanning method that is both dynamic and interactive, which enables it to discover more genuine vulnerabilities.
The conclusion is that the Netsparker web application security solution offers a comprehensive view of the state of your application’s safety. It offers support with the onboarding process as well as training. You will have greater visibility and deeper scans as a result of its distinctive DAST + IAST technique.
#7) System Mechanic Ultimate Defense
Best for Detecting Threats Using Artificial Intelligence and Algorithms.
Pricing for System Mechanic Ultimate Defense is set at $63.94 per year for the yearly plan.
Both an efficient computer optimizer and robust computer security programme, System Mechanic Ultimate Defense has you covered in both areas. Your personal computer will be protected in real time against spyware, viruses, and other similar dangers thanks to this real-time anti-virus protection. It does this by using intelligent threat detection algorithms and artificial intelligence to properly identify new and undiscovered dangers before they have the opportunity to do damage to your system.
Features
Helps prevent unauthorised users from accessing a user’s passwords and payment card information online.
Utilizes cutting-edge AI to identify and eliminate the most recent malware threats.
Locate and remove any bloatware that may be slowing down the system.
Utilize confidential technologies in order to investigate files that seem to be suspicious.
Conclusion: System Mechanic Ultimate Defense is essential to any discussion about computer security software and should never be left out. Because it makes use of very powerful artificial intelligence and algorithms, this software can recognise undiscovered new dangers in addition to those that have already been encountered. If you aren’t already aware of it, you should put this particular piece of cybersecurity software on your radar right now.
FAQ’s
What is the strongest cyber security?
Power in cyber defence: China tops the rankings in this area, followed by the Netherlands and France, then the United States and Canada in that order.
What equipment is needed for cyber security?
One (1) rack server that is built of ten (10) Dell PowerEdge 860 servers is included as part of the apparatus that is especially employed for cybersecurity procedures. a single instance of the Dell PowerEdge T100 Tower server. A single instance of the Sonicwall T2170 firewall.
Can you learn cyber security on your own?
Because of the abundance of online courses and other learning tools that are already accessible, it is now possible to educate oneself on cybersecurity on their own. For instance, prestigious educational institutions such as MIT, Harvard, Stanford, and many more institutions provide open courseware that may be used to study the fundamentals of cybersecurity from the very best of the very best educators.
Conclusion
We went through the best cybersecurity software products and discussed the need of maintaining a secure online presence. Free cybersecurity technologies such as Gnu Privacy Guard, Wireshark, and Snort are available. The CIS provides certain of its goods and services at no cost. Email security is provided by Mimecast, which includes effective spam detection and filtering capabilities. Snort is a platform that does real-time packet analysis and is entirely free to use.
Webroot offers security solutions not just for individuals but also for corporations and organisations. It offers a variety of products, such as DNS protection and Endpoint Protection, to commercial enterprises.
SolarWinds Threat Monitor is a system that is hosted in the cloud and provides Managed Service Providers with the ability to provide all-in-one solutions to their customers. Norton offers a wide range of different cybersecurity products, such as Virtual Private Networks (VPN), Antivirus Software, and Password Managers.